Spotting a Phish Easy tips on how to spot malicious emails.
October 4, 2017
 When most people hear the word “phishing”, the first thing that may come to mind is someone standing out in the middle of shallow river, casting a line and lure down stream. Unfortunately, this is not the case and cyber attackers work continuously around the clock finding ways into tricking online user to give them unrestricted access to their personal and financial information using a number of methods.
When most people hear the word “phishing”, the first thing that may come to mind is someone standing out in the middle of shallow river, casting a line and lure down stream. Unfortunately, this is not the case and cyber attackers work continuously around the clock finding ways into tricking online user to give them unrestricted access to their personal and financial information using a number of methods.

One of the most common methods used is sending malicious emails that look like good emails from a friend, colleague, or even a family member. Your natural inclination would be to assume that it is safe and that is exactly what they want you to think. But there are ways of spotting malicious emails before it is too late.
October is National Cybersecurity Awareness Month and our Information Security, here at Chapman University, would like to offer some quick and easy tips to help you “spot-a-phish”.
TIPS:
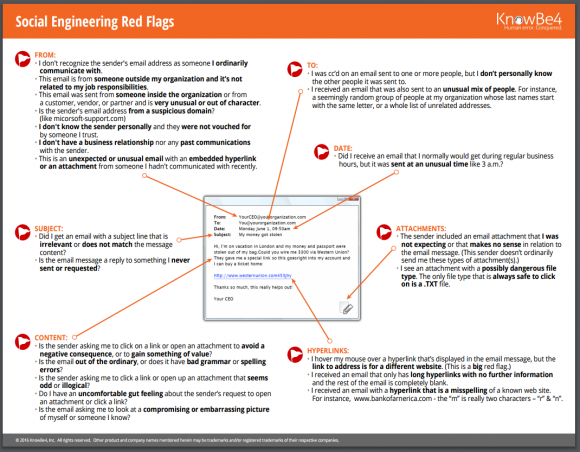
- Check the “From” field:
- Is the sender someone you are expecting an email from?
- Does the sender’s email address look suspicious?
- Do you recognize the website the sender is sending from?
- Check the “To” field:
- Are you being included on an email to other people you do not know or work with?
- Check the “Subject” field:
- Does the Subject match the actual content?
- Did you randomly “win” something you know nothing about?
- Read the “Content” carefully:
- SPELLING & GRAMMAR. Is the email using professional language and formatting, or does it seem rushed and unorganized?
- Are you being asked to click on something “before it’s too late”?
- Checking “Attachments” and “Hyperlinks” before you open them:
- When you hover your mouse over a hyperlink (without clicking), you can see the link’s website origin and domain information.
- Are there misspelled words on the hyperlink?
- Are you expecting the attachment from the sender?
- Is the attachment from a reliable / trustworthy source?
If you, at any time, feel you have received a suspicious email or would like to confirm the legitimacy of an email you received, please do not hesitate to contact IS&T for assistance. We highly encourage all Chaman University users to forward any suspicious emails to abuse@chapman.edu to be verified and blocked if needed. Another good practice is to periodically reset your password by visiting password.chapman.edu If you have any question or concerns regarding cyber safety, or if you are interested in some training, please contact infosec@chapman.edu.