Protecting Yourself When Interacting with Digital Files
June 7, 2022
Chapman University’s Information Security team has identified a new vulnerability that could affect MS Office users. This blog will review their findings, what Chapman is doing to protect the community, and share some best digital file and internet safety practices.
- New Vulnerability in Microsoft Office Applications (Word, Excel)
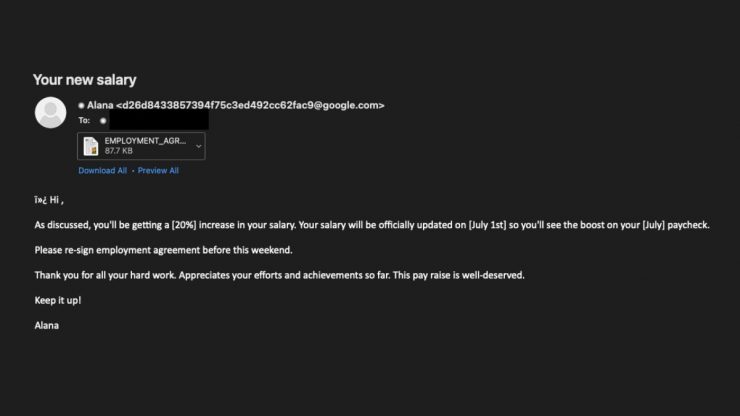
Microsoft has recently disclosed a vulnerability (CVE-2022-30190) that takes advantage of MS Office files such as Word and Excel and allows remote online attackers to potentially install programs, change the settings, delete data, and more. This new attack sometimes masquerades as a salary increase phish with attached files.
- How Protected View can help you stay safe
Microsoft’s Protected View, a feature in Microsoft Office that opens Office documents in read-only mode, can prevent this attack. Although Protected View provides safeguards by opening Office documents in read-only mode, it can be bypassed by enabling editing or by simply previewing a document that has been converted to Rich Text Format (RTF).
- Chapman University IS&T response
Chapman University’s Information Systems & Technology (IS&T) teams are actively monitoring this vulnerability and working on implementing additional preventive measures to protect the Chapman community.
- Tips to keep you safe every day
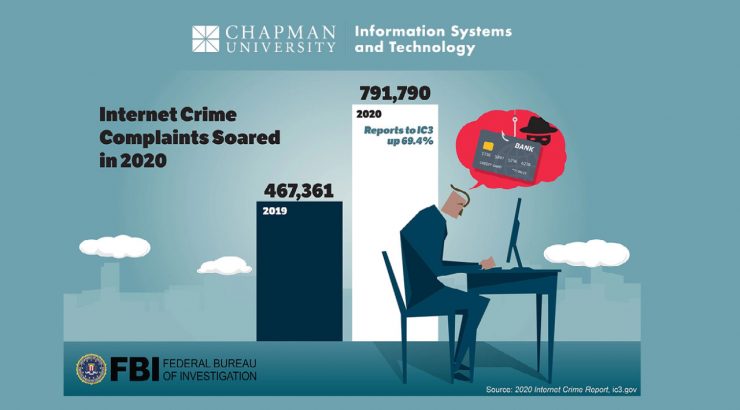
The rise in online interactions and digital file-sharing has led to an increase in people downloading digital files. It is not surprising that we are more likely to download something without thinking about it, especially since we have many devices and receive many emails every day.
We want to share a few tips on what to do before downloading files from the internet:
-
- Check the source: If the sender is using an email address that you do not recognize, try to confirm the sender’s identity. Navigate to websites directly from a browser and avoid links in emails when possible.
- Pay attention to file extensions: If you see a file extension you do not recognize, consider it dangerous. For example, .doc and .docx are two common extensions for Microsoft Word files, but sometimes hackers try to confuse you by using extensions that look similar such as .doxc. If you do not trust the source, do not download, preview, or open the file. Forward the email to Infosec for review if you are unsure.
- Slow down: Anytime you receive a new email from a source you do not recognize, slow down and run through the steps above. Also, if anyone asks you for sensitive information such as your passwords, social security number, etc., be curious and cautious.
- Use secure file sharing solutions such as Microsoft OneDrive, offered to all Chapman University students, faculty, and staff for free. Beware of shared cloud files when the sender’s name and email don’t appear to match.
- See something, report something
Chapman University’s Information Security team has a list of best practices and steps to protect yourself against Phishing. Finally, if you encounter an email that you think might be malicious, forward it to abuse@chapman.edu.
Thank you,
Chapman University Information Systems & Technology